The management of sensitive data in defense organizations is a complex task that necessitates secure storage, effective administration, and dependable access. Conventional centralized data management systems possess inherent weaknesses that make them prone to data breaches and unauthorized entry. However, blockchain technology provides a decentralized, unchangeable, and transparent platform that can augment the security, integrity, and traceability of defense data management. The objective of this study is to investigate the feasibility of employing a blockchain-powered web client named BlockDef for managing defense data. It will present an analysis of the primary obstacles, advantages, and factors to consider in implementing such a system.
The management of defense data is of utmost significance in military and defense organizations due to the critical and sensitive nature of the information involved. It

Figure 1:The cost of cyber attacks At Different Countries Of The World .
involves various vital tasks, including data collection, storage, processing, analysis, and distribution, covering aspects such as military operations, intelligence, personnel, logistics, and more. The efficacy of defense data management directly influences strategic decision-making, operational efficiency, mission triumph, and ultimately safeguards the overall security of a nation.
Elevating security measures stands as an imperative priority in defense data management. Constantly besieged by cyber attacks[1], espionage endeavors, and unauthorized access attempts, defense organizations face perpetual threats. A breach in data security can result in severe ramifications, including compromised military operations, intelligence leaks, jeopardized personnel safety, and significant harm to national security. Ensuring the protection of classified and sensitive information necessitates the implementation of robust security measures and encryption protocols, acting as steadfast guardians against malevolent actors.
Efficiency constitutes another vital facet of defense data management. Given the multitude of sources from which defense organizations amass copious amounts of data, such as surveillance systems, sensor networks, intelligence gathering, and operational records, the seamless management of this data becomes indispensable. By ensuring efficient data management, organizations enable timely and precise analysis, facilitate informed decision-making, and foster seamless information sharing. The optimization of data processes, integration of disparate systems, and the application of advanced analytics and automation techniques serve as catalysts for heightened operational efficiency and agility.
Moreover, effective defense data management actively supports collaboration and information sharing across diverse military branches, allied forces, intelligence agencies, and defense contractors. The timely and secure exchange of data plays a pivotal role in joint operations, intelligence sharing, and synchronized response efforts. By emphasizing improved interoperability, standardized data formats, and secure communication channels, defense organizations can forge a cohesive environment conducive to effective collaboration, thereby ensuring the accomplishment of missions.
In essence, the significance of defense data management lies in its profound impact on national security, military operations, and decision-making processes. Bolstered security measures and increased efficiency in managing defense data are indispensable elements in safeguarding sensitive information, sustaining operational readiness, and fortifying the effectiveness of defense organizations within an evolving threat landscape driven by complexity and digitalization.
Architecture for a Blockchain-Based Web Client for Defense Data Management:
The design of a defense data management web client based on blockchain technology consists of the following components:
- User Interface: The web client[9] provides an intuitive interface for defense personnel to securely access, view, and manage data. The interface should be user-friendly, responsive, and prioritize ease of use.
- Blockchain Network[10]: The blockchain network acts as a decentralized ledger[11] for storing and managing defense data. It includes multiple nodes that store copies of the blockchain.
- Depending on data privacy requirements, the network can be public, private, or a consortium blockchain[12].
- Data Storage and Encryption: Defense data is securely stored on the blockchain. Sensitive data can be encrypted before adding it to the blockchain to ensure confidentiality. Encryption methods like asymmetric cryptography[13] are used to protect the data while allowing authorized access.
- Smart Contracts[14]: Smart contracts[14] are programmable code executed on the blockchain. They can be employed to enforce data access control and automate validation processes. Smart contracts establish rules and conditions for accessing and manipulating data, ensuring that only authorized personnel can access specific information. These contracts can automate validation procedures, guaranteeing that data meets predefined criteria before being added to the blockchain.
- Integration with Existing Systems: The blockchain-based web client seamlessly integrates with existing defense systems and databases. This enables smooth data exchange through APIs, connectors, or middleware, ensuring compatibility and interoperability with legacy systems.
- Enhance Security from Attackers: Blockchain Based web client enhance security from attacker’s by empowering the strong security to the system.
| serial No | Blockchain Based Used Algorithms | Advantage of System |
| 1 | IPFS | Decentralized and efficient file storage and sharing with cryptographic integrity checks. |
| 2 | Zero Knowledge proof | Secure and private user management with Zero-Knowledge Proofs (ZKPs). |
Proposed Defence File Management System BlockDef
We introduce BlockDef, an innovative web client created specifically for secure defense file management. BlockDef utilizes the InterPlanetary File System (IPFS)[15] for storage and incorporates zero-knowledge proof authentication[16] to guarantee strong security and privacy for sensitive defense documents. This research paper offers a detailed examination of the BlockDef system architecture, emphasizing its essential elements, features, and security measures. Through experimental evaluation, the study validates BlockDef’s effectiveness in terms of security, performance, and user-friendliness. The findings affirm BlockDef’s potential as a dependable and
efficient file management solution for the defense industry.In order to uphold the confidentiality, integrity, and accessibility of sensitive defense files, effective management and secure storage are crucial. However, conventional file management systems encounter notable hurdles in terms of security and scalability. To overcome these limitations, we present BlockDef, a secure web client that integrates IPFS[15] as its storage system and incorporates zero-knowledge proof[16] authentication to bolster security measures. It provides an overview of the security measures incorporated in BlockDef to protect defense files and user credentials. It includes encryption methods, access control strategies, secure communication protocols, and data integrity verification, all designed to prevent unauthorized access and tampering.

Fig-2: BlockDef Concept Project Builded In Python.
BlockDef utilizes IPFS as its underlying storage system, taking advantage of its decentralized and distributed nature. This section explains how BlockDef leverages IPFS to store defense files securely, ensuring redundancy, immutability, and efficient retrieval. It also incorporates zero-knowledge proof authentication to provide a robust and privacy-preserving login mechanism. This section discusses the underlying principles of zero-knowledge proofs and explains how they are employed in BlockDef to authenticate users without revealing sensitive information.
Mechanism of Proposed Project BlockDef
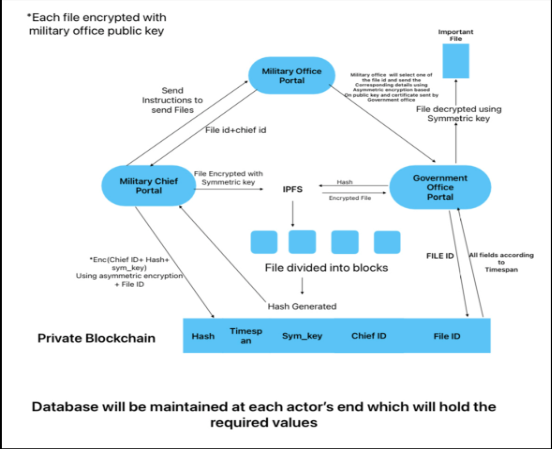
We designed a system where we use IPFS to achieve decentralization and secure peer-to-peer communication[17] between Military Chief And Government Office. Encrypting files and our packets to ensure more safety is also used in python framework, for compatibility. The web development is done with the help of Django[18].
A quick walkthrough of the project:
- The military office from the datasheet in its local storage send instructions to to the designated military chief to send important files
- As the military office send the instructions to the military chief, they accept it and download the instruction pdf to their local machine.
- After getting instructions, the military chief set the important files and upload it to the server in pdf format to send the file.
- Now this pdf file when prepared and encrypted with symmetric key, is sent to the distributed file system which is IPFS
- IPFS divides the file into various chunks. These chunks are stored on a decentralized server and each chunk’s hash is generated. The hashes are combined to give one hash to retrieve the file
- Further, this hash along with other particulars is sent to be stored in block chain ledger
- Submitted papers start showing on Military Office portal without any details of file and chief. So military office finalizes the file and sends to Government Office.
- The government office receives these details. Government office gets details of file retrieval from block chain ledger.
- After getting the details automatic request to retrive file from IPFS is sent and then government office gets the original paper.

Fig-3: Diagram of File Management mechanism of BlockDef
Uses of Zero-Proof Authentication in BlockDef
In BlockDef Zero-knowledge proof methods are utilized to bolster the privacy and security of user credentials. The User model incorporates a zero-knowledge proof field, which contains a cryptographic proof validating the user’s identity without disclosing any sensitive information. This ensures that even in the event of a system breach, user data remains safeguarded. By the application of zero proof authentication[19] , the proposed system eradicates vulnerabilities associated with single points of failure and guarantees data immutability. This ensures that unauthorized alterations to user data become highly impractical, offering robust protection against common attack methods such as data tampering[20] and replay attacks[21].

Unit Testing:
Unit Testing is a software testing approach that focuses on testing individual components or units of software to ensure they perform according to their design. It involves testing various modules separately to validate their functionality. In our project, we had three modules, each with its own testing process.
- For the Blockchain Module, we conducted tests specifically on the blockchain system to ensure that all provided functionalities were functioning correctly. Initially, we implemented Hyperledger Fabric for the blockchain network and tested transactions within the Blockchain Ledger. The outcome of the testing was successful.
- In the Web + Data Storage Module, we performed tests to verify the proper functioning of front-end functionalities on the website and to ensure that all data involved in the system was stored correctly in either the local or online distributed database. The testing results indicated successful implementation.
- The Security Module underwent testing to assess the effectiveness of security enhancement techniques, such as symmetric and asymmetric encryption, and to identify any potential vulnerabilities in these methods. The testing concluded with successful results.
Overall, the unit testing process for each module confirmed the successful implementation of the functionalities and security measures within the system.
System Testing:
System Testing is a software testing method that evaluates the overall compliance of a fully integrated system with its defined requirements. Following the integration testing phase, we explored alternative approaches to integrate the Blockchain module with the (web+security) module and discovered that Hyperledger Composer could facilitate seamless interaction between the web and Blockchain server. As a result, all system functionalities are functioning in accordance with the specified requirements. The outcome of the system testing was successful.
- uccessful.
- In the Web + Data Storage Module, we performed tests to verify the proper functioning of front-end functionalities on the website and to ensure that all data involved in the system was stored correctly in either the local or online distributed database. The testing results indicated successful implementation.
- The Security Module underwent testing to assess the effectiveness of security enhancement techniques, such as symmetric and asymmetric encryption, and to identify any potential vulnerabilities in these methods. The testing concluded with successful results.
Overall, the unit testing process for each module confirmed the successful implementation of the functionalities and security measures within the system.
System Testing:
System Testing is a software testing method that evaluates the overall compliance of a fully integrated system with its defined requirements. Following the integration testing phase, we explored alternative approaches to integrate the Blockchain module with the (web+security) module and discovered that Hyperledger Composer could facilitate seamless interaction between the web and Blockchain server. As a result, all system functionalities are functioning in accordance with the specified requirements. The outcome of the system testing was successful.

(b)

RESULTS
Instruction Transmission:
- The military office successfully sends instructions to the designated military chief through the local storage system.
- The transmission of instructions occurs securely, ensuring that the information remains confidential and is not intercepted or tampered with during the process.
Instruction Download and Assessment:
- The designated military chief securely retrieves the instructions and effectively downloads the instruction PDF onto their local device.
- The military chief carefully examines the content and comprehends the information and obligations specified in the document.
File Upload and Encryption:
- Following the given instructions, the military chief gathers the essential files and proceeds to upload them to the server in PDF format.
- To ensure the confidentiality and integrity of the uploaded PDF file during transmission, it undergoes encryption utilizing a symmetric key encryption algorithm.
IPFS Storage and Chunking:
- The encrypted PDF file is securely transmitted to the IPFS (InterPlanetary File System) for storage and dissemination purposes.
- IPFS breaks down the file into several smaller chunks and distributes them across a decentralized network of servers.
- Hash values are generated for each individual chunk, and these hashes are combined to create a single hash that represents the entirety of the file.
Blockchain Ledger Integration:
- The composite hash of the file, alongside other pertinent details, is stored within a blockchain ledger to establish a secure and immutable record.
- The integration with the blockchain ledger ensures the preservation of data integrity and prevents any unauthorized tampering with the file-related information.
Secure Access on Military Office Portal:
- The Military Office portal grants access to the submitted documents, without disclosing any specific details about the file or the military chief.
- The Military Office undertakes the verification and finalization process to ensure the file’s appropriateness and compliance with regulations and requirements.
File Retrieval by Government Office:
- Upon receiving the file details from the Military Office, the Government Office utilizes the information stored in the blockchain ledger.
- Using this information, an automated request is initiated by the Government Office to retrieve the file from IPFS.
PROJECT SOURCE CODE