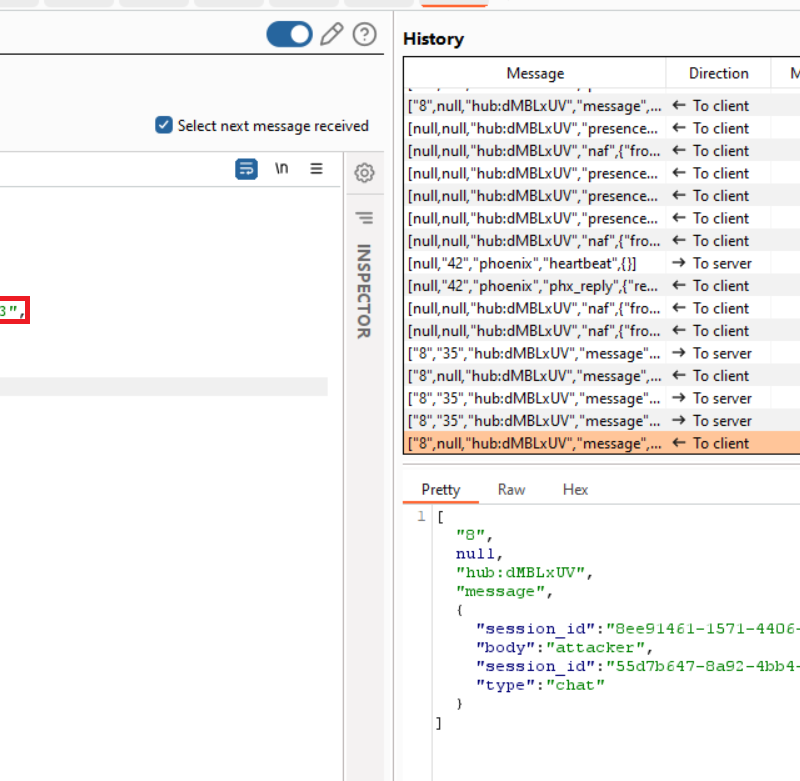
IDOR – send a message on behalf of other user
I just found an IDOR in https://hello.dev.myhubs.net/. It allow attacker send a message on behalf of other user Step to reproduce: Admin: Create Room Attacker: Join room Attacker get "session_id" of other user in response "presence_diff" Attacker send add "session_id" parameter to request send message ["8",null,"hub:84fbckn","message",{"session_id":"<victim_session_id>","body":"eeeee","type":"chat"}] Now the message will be send on behalf of victim