Target: Brave Software
Title: New XSS vector in ReaderMode with %READER-TITLE-NONCE%
Summary:
Previously, script execution in ReaderMode pages was prohibited by CSP. However, three months ago, this commit partially relaxed the CSP and scripts with nonce-%READER-TITLE-NONCE% are now allowed to be executed. This relaxation of the CSP rule can be exploited for XSS attacks on ReaderMode pages.
Here, the attack vector is %READER-CREDITS% which is also included in the ReaderMode HTML template. The %READER-CREDITS% is replaced with the value of the <meta name=”author”> tag in the original page, but then the HTML tags are not escaped. So, when the following meta tag is embedded in the original page and the page is displayed in ReaderMode, this Swift code replaces %READER-TITLE-NONCE% with the correct noice.
<meta name=”author” content=”Evil <script nonce=%READER-TITLE-NONCE%>alert(document.location);</script>!–“>
As a result, the malicious script will be executed on a page http://localhost:6571/reader-mode?uri={uri}&uuidkey={value}. In Brave, all readalized pages are hosted on http://localhost:6571. Therefore, through this XSS, any cross-origin pages, that has been converted to ReaderMode, can be stolen by embedding an iframe and reading out them. Also, please find that the uuidkey is included in the URL query string. By obtaining this key, the attacker can gain access to Brave’s privileged pages.
Products affected:
Brave iOS 1.31.1 and higher (including the latest Nightly)
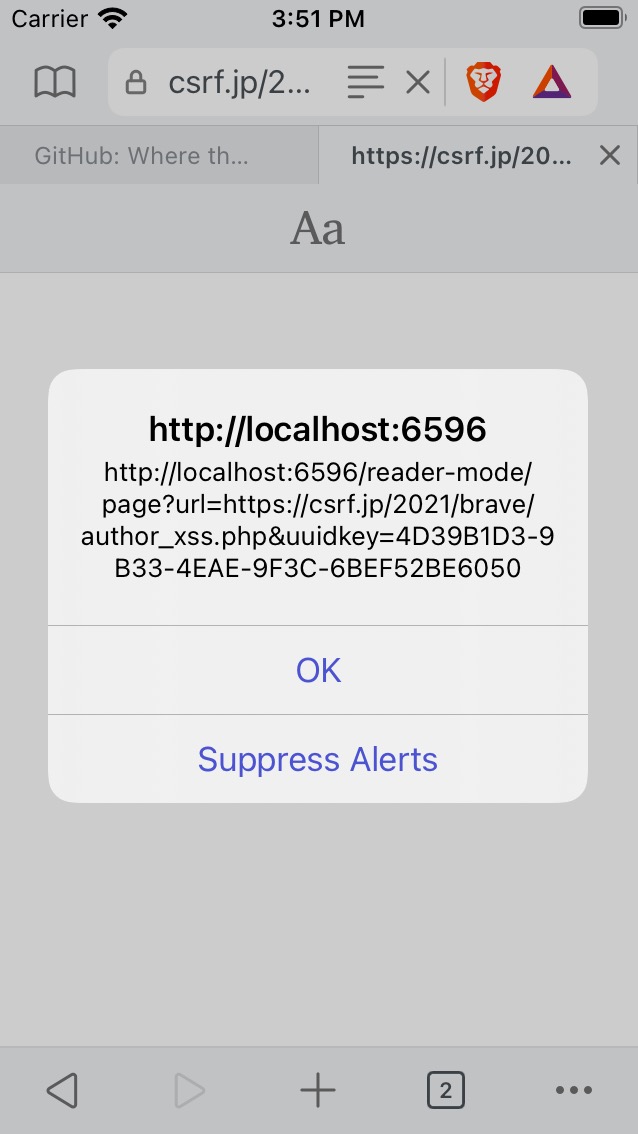
Steps To Reproduce:
1)Show https://csrf.jp/2021/brave/author_xss.php
2)Push reader mode button on the address bar
3)An alert dialog is shown
Impact:
1)Any cross-origin pages, that has been converted to ReaderMode, can be stolen